Not so long back I published a blog on Getting an A+ rating on the Qualys SSL Test, which I recently updated to keep in line with the latest requirements on RC4 ciphers and SHA1/SHA256 certificates. Since then, I've had a few questions from people who were getting the A+ rating but not getting quite the same score despite having the same protocols and ciphers defined. Here's how you do it, and don't worry, it's pretty easy.
The difference
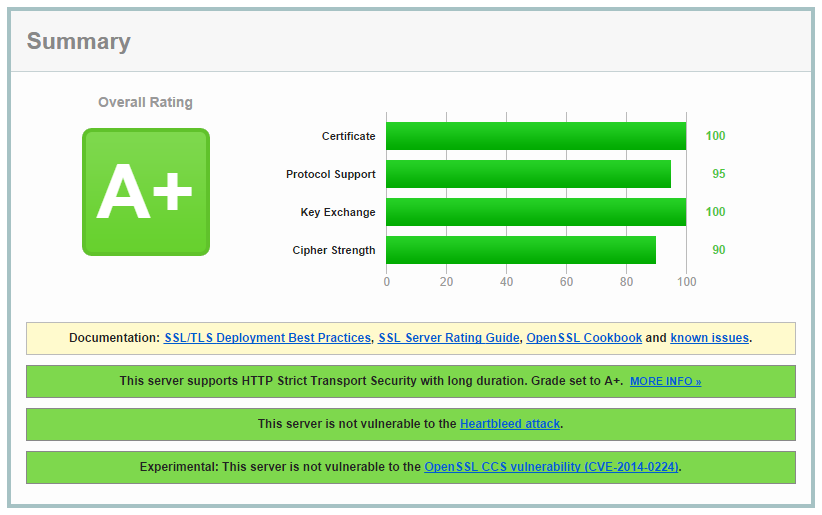
I'm going to use my blog and one of my other sites (EVS) to demonstrate the difference that people have been asking about. Here is the Qualys test for my blog:
Here's the result for EVS:
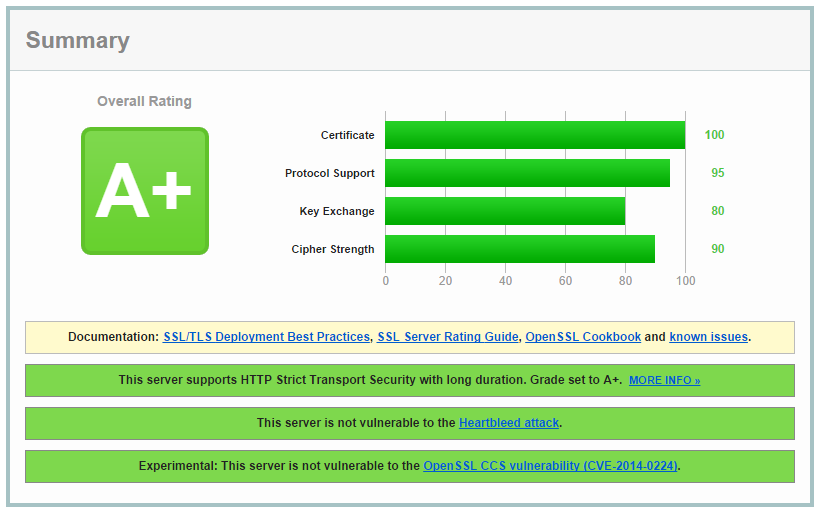
As you can see, there is quite a difference in the Key Exchange score, yet these 2 installations of nginx are using the exact same cipher suites.
ssl_ciphers ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS;
Diffie-Hellman parameters
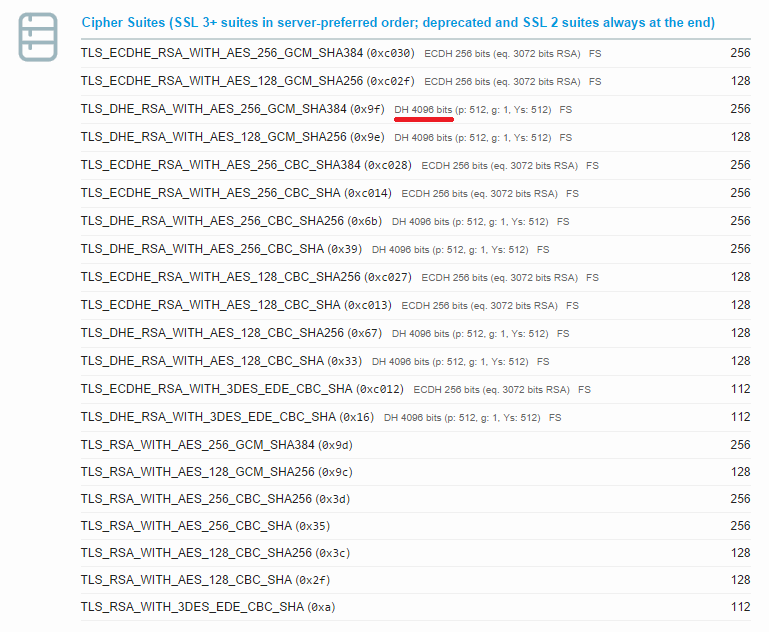
Nginx uses OpenSSL's default 1024 bit key size as an input to the DH key exchange, resulting in a 1024 bit key. Ideally, we should be using a key no smaller than our SSL certificate which is commonly 2048 or even 4096 bits. To increase the Key Exchange score, we need to increase the size of the key used in the DH exchange. You can see the size of the key currently being used in the Cipher Suites section of the Qualys Test. I have underlined the appropriate value in red on my blog result:
Here is the result for EVS with the value underlined again:
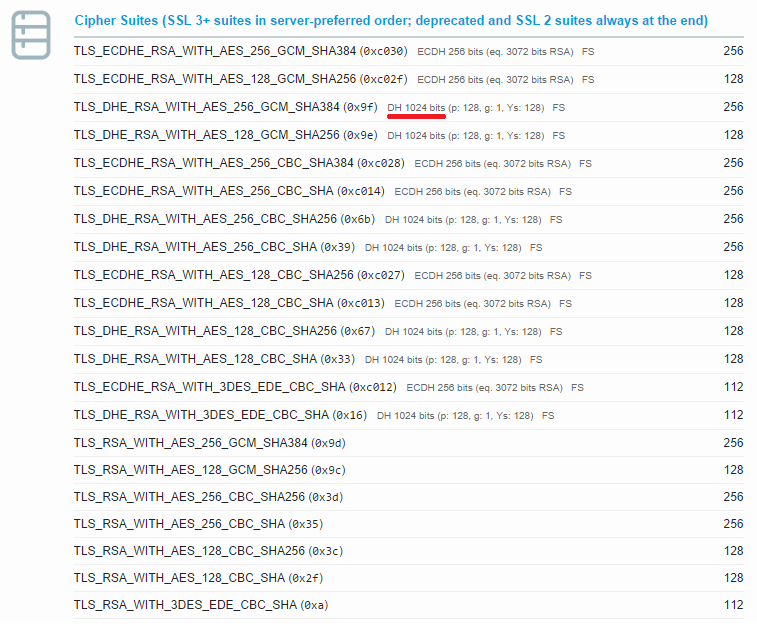
You can see the difference in the 2 configurations and this is the result of the difference in the Key Exchange score.
Generate stronger parameters
All we need to do to fix this is up is issue a few simple commands. We're going to generate a new set of DH parameters and store them in a file, so move to the directory where you want to store it. I used the same directory as my SSL certificate and key file.
cd /etc/nginx/conf/ssl/evstatus.com
Next up we need to ask OpenSSL to make the new parameters for us.
openssl dhparam -out dhparam.pem 4096
You can drop the size down to 2048 bits if you like, but this mainly depends on the key size in your SSL certificate. This command will take a while to run, so don't worry. On my DigitalOcean VPS it took over an hour!
Once that's done, we need to tell nginx to use the new DH parameters. Open up your virtual host file and right below where you define your ssl_protocols and ssl_ciphers you need to add a new directive:
ssl_dhparam /etc/nginx/conf/evstatus.com/dhparam.pem;
Once that's in there, save the file and reload your nginx configuration:
sudo service nginx reload
Once nginx has reloaded the configuration, hit the Qualys SSL test again and you should now score 100 in the Key Exchange!
Here are the tests for my blog and EVS which now both score exactly the same.
Note:
As mentioned in my article on Getting an A+ rating on the Qualys SSL Test, Qualys are currently penalising sites that use a SHA1 certificate as the leaf or in the certificate chain at the time of writing. This will reduce your score from an A+ to an A and this is what you will see.
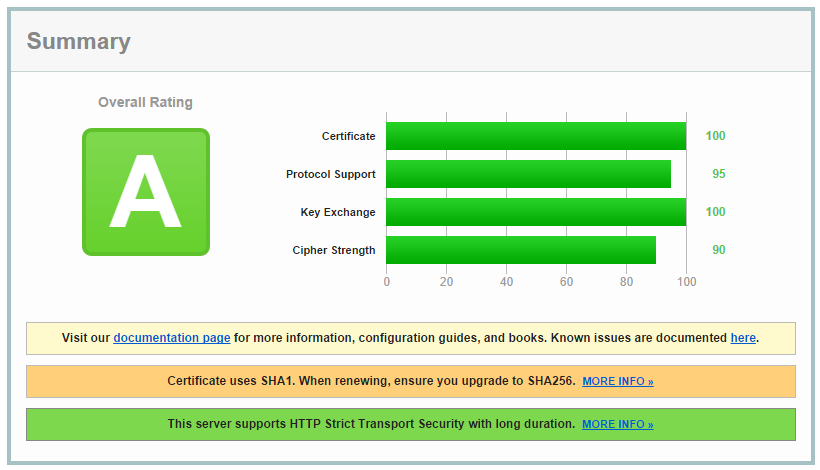
The only resolution is to revoke your existing certificate and have a new one issued using SHA256. You will most likely also need to update your certificate chain to contain only SHA256 certificates too! If you use StartCom as your CA like I do, you can find all the certificates you need here.
