Password guidance: executive summary
Published 8 September 2015
1. Introduction
Password guidance - including previous CESG guidance - has encouraged system owners to adopt the approach that complex passwords are ‘stronger’. However, complex passwords do not usually frustrate attackers, yet they make daily life much harder for users. They create cost, cause delays, and may force users to adopt workarounds or non-secure alternatives that increase risk.
This guidance contains advice for system owners responsible for determining password policy. It is not intended to protect high value individuals using public services. It advocates a dramatic simplification of the current approach at a system level, rather than asking users to recall unnecessarily complicated passwords.
1.1 The problems with passwords
The increase in password use is mostly due to the surge of online services, including those provided by government and the wider public sector. This proliferation of password use, and increasingly complex password requirements, places an unrealistic demand on most users. Inevitably, users will devise their own coping mechanisms to cope with ‘password overload’. This includes writing down passwords, re-using the same password across different systems, or using simple and predictable password creation strategies.
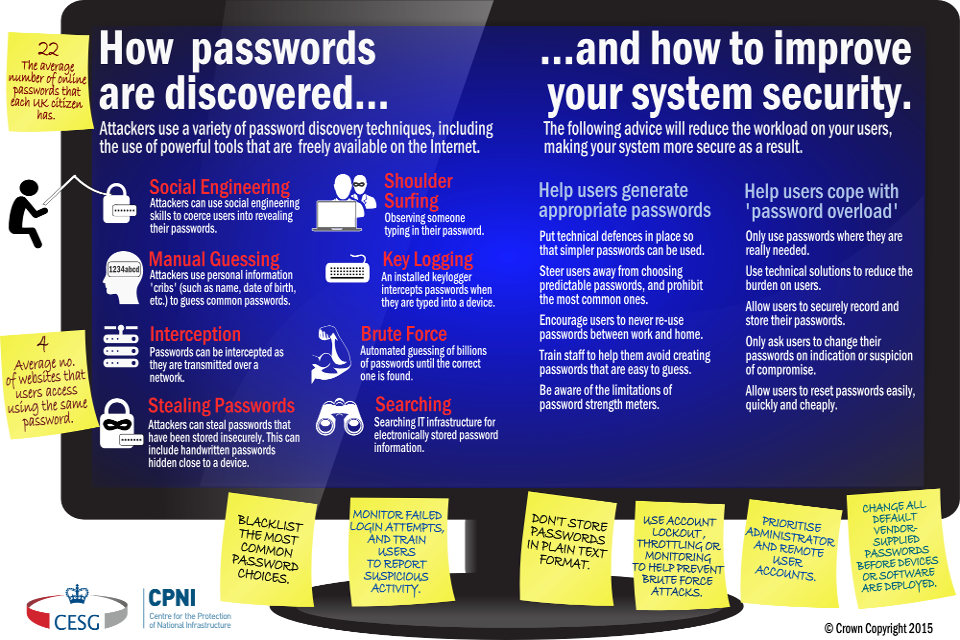
1.2 How passwords are discovered
Attackers use a variety of techniques to discover passwords, which include:
- social engineering eg phishing; coercion
- manual password guessing, perhaps using personal information ‘cribs’ such as name, date of birth, or pet names
- intercepting a password as it is transmitted over a network
- ‘shoulder surfing’, observing someone typing in their password at their desk
- installing a keylogger to intercept passwords when they are entered into a device
- searching an enterprise’s IT infrastructure for electronically stored password information
- brute-force attacks; the automated guessing of large numbers of passwords until the correct one is found
- finding passwords which have been stored insecurely, such as handwritten on paper and hidden close to a device
- compromising databases containing large numbers of user passwords, then using this information to attack other systems where users have re-used these passwords
2. Password guidance at-a-glance
2.1 Tip 1: Change all default passwords
Factory-set default passwords being left unchanged is one the most common password mistakes that organisations make. By leaving default credentials in place, networking and critical infrastructure is reachable online.
- Change all default passwords before deployment.
- Carry out a regular check of system devices and software, specifically to look for unchanged default passwords.
- Pay particular attention to critical infrastructure devices such as routers, wireless access points, and firewalls.
2.2 Tip 2: Help users cope with password overload
Users are generally told to remember passwords, and to not share them, re-use them, or write them down. But the typical user has dozens of passwords to remember – not just yours. Regular password changing harms rather than improves security, so avoid placing this burden on users. However, users must change their passwords on indication or suspicion of compromise.
- Only use passwords where they are really needed.
- Use technical solutions to reduce the burden on users.
- Allow users to securely record and store their passwords.
- Only ask users to change their passwords on indication or suspicion of compromise.
- Allow users to reset passwords easily, quickly and cheaply.
- Do not allow password sharing.
- Password management software can help users, but carries risks.
2.3 Tip 3: Understand the limitations of user-generated passwords
User-generated password schemes are more commonly used than machine-generated ones, due to being cheaper and quicker to implement. However, user-generated password schemes carry risks that machine-generated schemes do not. Most dictionaries for brute-force attacks will prioritise frequently used words and character substitutions, so systems with user generated passwords will normally contain a large, number of weak passwords that will quickly fall to an automated guessing attack.
- The use of technical controls to defend against automated guessing attacks is far more effective than relying on users to generate (and remember) complex passwords.
- Put technical defences in place so that simpler password policies can be used.
- Reinforce policies with good user training. Steer users away from choosing predictable passwords, and prohibit the most common ones by blacklisting.
- Tell users that work passwords protect important assets; they should never re-use passwords between work and home.
- Be aware of the limitations of password strength meters.
2.4 Tip 4: Understand the limitations of machine-generated passwords
Machine-generated passwords eliminate those passwords that would be simple for an attacker to guess. They require little effort from the user to create, and, depending on the generation scheme, can produce passwords that are fairly easy to remember. However, some machine generation schemes can produce passwords which are very difficult for people to remember. This increases both the demand on helpdesk for resets, and also the likelihood of insecure storage. They are not recommended.
- Technical controls such as account lockout, throttling or protective monitoring are still relevant when using machine-generated passwords.
- Choose a scheme that produces passwords that are easier to remember.
- Offer a choice of passwords, so users can select one they find memorable. Examples of these include passphrases, 4 random dictionary words, and CVC-CVC-CVC style passwords (cvc = consonant-vowel-consonant).
- As with user-generated passwords, tell users that work passwords protect important assets; they should never re-use passwords between work and home.
2.5 Tip 5: Prioritise administrator and remote user accounts
Administrator accounts have highly privileged access to systems and services. Compromise of these accounts is a threat to the wider system, and therefore especially attractive to attackers.
- Give administrators, remote users and mobile devices extra protection.
- Administrators must use different passwords for their administrative and non-administrative accounts.
- Do not routinely grant administrator privileges to standard users.
- Consider implementing two factor authentication for all remote accounts.
- Make sure that absolutely no default administrator passwords are used.
2.6 Tip 6: Use account lockout and protective monitoring
Account lockout, throttling, and protective monitoring are powerful defences against brute-force attacks on enterprise systems and online services. Password systems can be configured so that a user only has a limited number of attempts to enter their password before their account is locked out. Or, the system can add a time delay between successive login attempts - a technique known as ‘throttling’.
- Account lockout and ‘throttling’ are effective methods of defending brute-force attacks.
- Allow users around 10 login attempts before locking out accounts.
- Password blacklisting works well in combination with lockout or throttling.
- Protective monitoring is also a powerful defence against brute-force attacks, and offers a good alternative to account lockout or throttling.
- When outsourcing, contractual agreements should stipulate how user credentials are protected.
2.7 Tip 7: Don’t store passwords as plain text
Passwords should never be stored as plain text, even if the information on the protected system is relatively unimportant. An attacker who gains access to a database containing plain text passwords already knows a user’s credentials for one system. They can use this information to attempt to access more important accounts, where further damage can be done.
- Periodically search systems for password information that is stored in plain text.
- Never store passwords as plain text.
- Produce hashed representations of passwords using a unique salt for each account.
- Store passwords in a hashed format, produced using a cryptographic function capable of multiple iterations (such as SHA 256).
- Ensure you protect files containing encrypted or hashed passwords from unauthorised system or user access.
- When implementing password solutions use public standards, such as PBKDF2, which use multiple iterated hashes.
