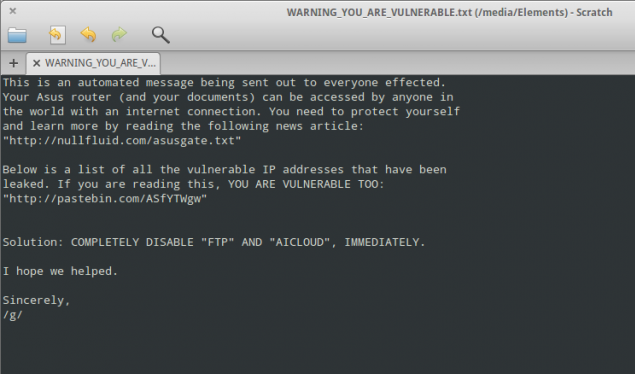
An Ars reader by the name of Jerry got a nasty surprise as he was browsing the contents of his external hard drive over the weekend—a mysterious text file warning him that he had been hacked thanks to a critical vulnerability in the Asus router he used to access the drive from various locations on his local network.
"This is an automated message being sent out to everyone effected [sic]," the message, uploaded to his device without any login credentials, read. "Your Asus router (and your documents) can be accessed by anyone in the world with an Internet connection. You need to protect yourself and learn more by reading the following news article: http://nullfluid.com/asusgate.txt."
It's likely that Jerry wasn't the only person to find the alarming message had been uploaded to a hard drive presumed to be off-limits to outsiders. Two weeks ago, a group posted almost 13,000 IP addresses its members said hosted similarly vulnerable Asus routers. They also published a torrent link containing more than 10,000 complete or partial lists of files stored on the Asus-connected hard drives.
The guerilla-style hacking disclosure comes eight months after a security researcher publicly disclosed the underlying vulnerability that exposed the hard drives of Jerry and so many other Asus router users. The June 22 report found the "ability to traverse to any external storage plugged in through the USB ports on the back of the router," but researcher Kyle Lovett said he went public only after privately contacting Asus representatives two weeks earlier and getting a response that the reported behavior "was not an issue." In July, Lovett published a second disclosure that offered additional technical details.
"The vulnerability is that on many, if not on almost all N66U units that have enabled https Web service access via the AiCloud feature, [they] are vulnerable to un-authenticated directory traversal and full sensitive file disclosure," Lovett wrote in his earlier dispatch. "Any of the AiCloud options 'Cloud Disk,' 'Smart Access,' and 'Smart Sync' (need another verification on this one) appear to enable this vulnerability."
According to Lovett, the weakness affects a variety of Asus router models, including the RT-AC66R, RT-AC66U, RT-N66R, RT-N66U, RT-AC56U, RT-N56R, RT-N56U, RT-N14U, RT-N16, and RT-N16R. Asus reportedly patched the vulnerabilities late last week, but as Jerry's experience demonstrates, it has yet to be installed on some vulnerable routers.
"Needless to say, I am pissed," he wrote in a message to Ars. He went on to say that he thought his device was secure because he hadn't enabled any services that explicitly made hard drive contents available over the Internet. "It was my belief that I had all of these options turned off," he said. "I definitely have never used AICloud or had it enabled. In fact, the only thing I've ever enabled myself is the Samba share. However, the Asus menu is very unclear about what is being shared and with whom."
He's not the only one to face the rude discovery that contents of his Asus-attached hard drive have been available to anyone with some rudimentary knowledge and a standard Internet connection. Earlier this month, a Harvard Law School blogger was shocked to find that he was also caught with his digital pants down after hooking a "giant USB drive" to his RT model Asus router.
"Out of curiosity, I entered 'ftp://[my external ip address]' into my browser and sat wide eyed when I saw the contents of my media server show up," the blogger wrote. "I reasoned it must be because I’m already inside the network (which doesn’t even make sense really), but panic was starting to set in. So I pulled out my phone and turned off the Wi-Fi connection and tried it there. Now I was worried."
The exploits against the Asus router coincide with the discovery of a round of attacks that infect Linksys routers with self-replicating malware. The Linksys exploits don't expose any user data, and infected machines can be restored to their normal state by being rebooted. The in-the-wild exploits against both Asus and Linksys devices come two weeks after researchers in Poland reported an ongoing attack that stole online banking credentials in part by modifying home routers' DNS settings.Taken together, the attacks are a sign that routers and other Internet-connected devices are being subject to the same in-the-wild attacks that have plagued PCs—and in some cases Macs—for years. Readers are advised to lock down their routers by installing any available firmware updates, changing any default passwords, and ensuring that remote administration, Cloud, and FTP options are set to off if they're not needed.
reader comments
181